Ethical Hacking Institute Course in Pune-India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan
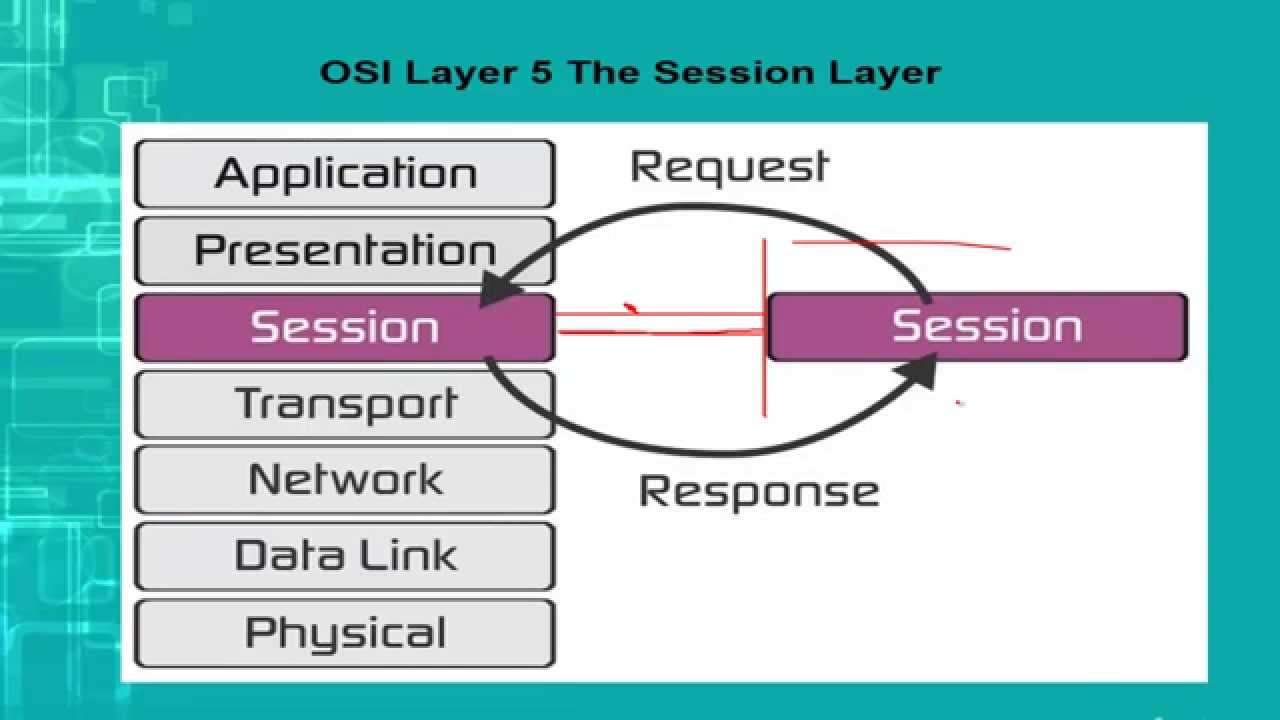
As we talked earlier in the article OSI Model and its 7 layers, the session layer is an important layer as it is responsible for maintaining, authorizing and authenticating a session between two end-user applications.
Have you ever wondered how your PC maintains a connection with the server? How does your PC know that the destination it communicates to is a legitimate one? Well, the session layer has the all the answers.
So, let’s go further and take a look into what all basic things session layer does and what protocols are run at the session layer.
Session layer functionalities:
-
Session management
As its name suggests, the session layer is responsible for managing a session which includes opening, closing and managing a session between end-user application processes. You can think of session layer as the main layer which handles the requests and responses between the two applications.
For example, if you are downloading some pictures from Facebook, a network path is defined by the network layer but the requests for the photos and responses by Facebook to you is handled by the session layer.
If you have heard of HTTP 1.0 or HTTP 1.1, these application layer protocols somehow follow the session layer orders in delivering the data.
-
Authentication
Before establishing a session with some network peer, it is important for one of the computers to know that another peer it is communicating to is a legitimate one. In short terms, you can say that authentication is the process of verifying that “you are who you say you are”.
-
Authorization
Authorization is more like “Are you authorized to do so?”
Here is an example:
If someone knows my email address and password, he can easily authenticate himself as ‘Amar Shekhar’ and he can log in as well. However, since he is not the right person to access my personal email account, so he is not an authorized person to do so.
So the basic difference between the two is: authentication is the process of verifying that “you are who you say you are”, authorization is the process of verifying that “you are permitted to do what you are trying to do”. Authorization thus presupposes authentication.
Some of the famous session layer’s protocols are:
- Remote procedure call protocol (RPC)
- Point-to-Point Tunneling Protocol (PPTP)
- Session Control Protocol (SCP)
- Session Description Protocol (SDP) etc.
www.extremehacking.org
Cyber Suraksha Abhiyan, CEHv9, CHFI, ECSAv9, CAST, ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v9 course in Pune-India, ceh certification in pune-India, ceh v9 training in Pune-India, Ethical Hacking Course in Pune-India
