Ethical Hacking Institute Course in Pune-India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan
We often seek the help of a program or a tool in doing small things in our Windows like cleaning a drive, managing the firewall etc. However, these things, up to a level, are also possible if you are aware of the basic CMD commands.
After covering topics like how to kill a remote connecting malware on Windows and how to create bootable USB in Windows from the command line, today, we are going to talk about a command and its variants to monitor network and network traffic on Windows. Yes, we are talking about the Netstat command.
As its name suggests, netstat command is a short form for network statistics. However, this short command has a lot of capabilities to find a large amount of information about our network such as ports, their status, connections (incoming and outgoing), protocols and much more information.
List of Netstat commands to monitor network on Windows
-
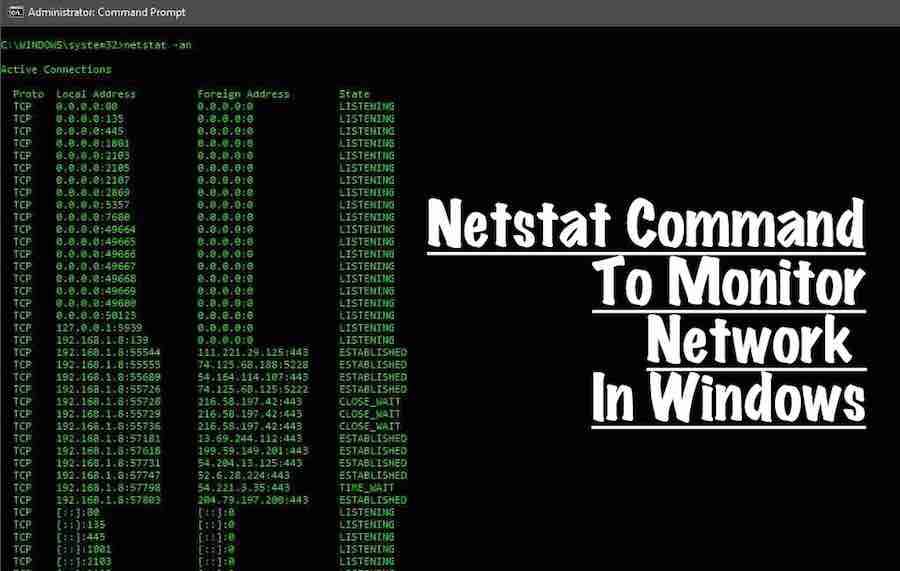
netstat
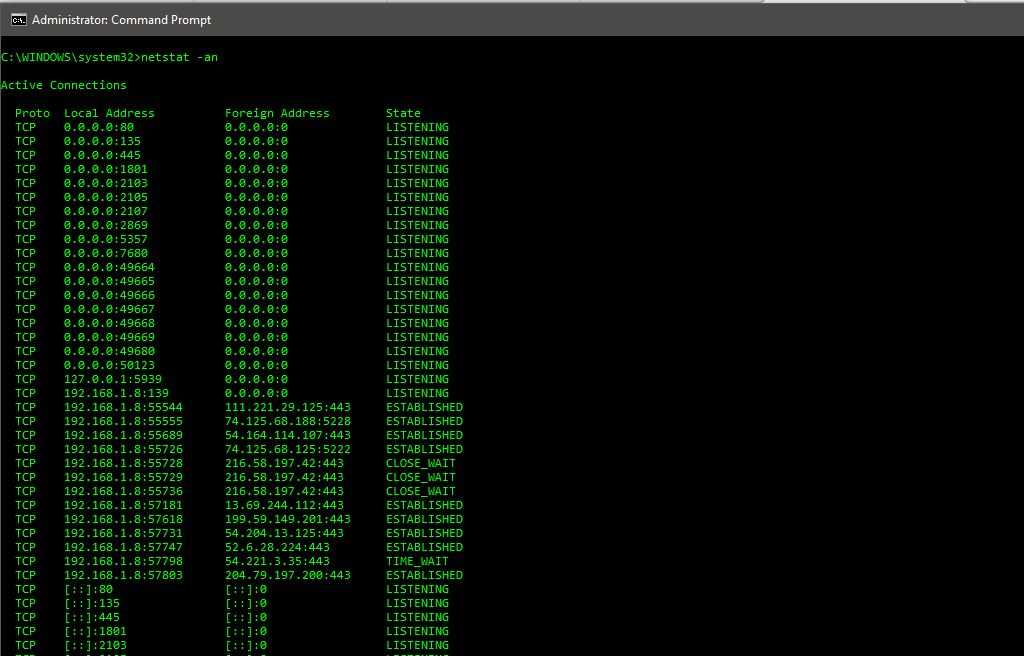
As you can see above, this command will display the state all of the connections from your computer. You can see that local address and the foreign address are in the raw format.
It disables the DNS lookups as it takes time and it’s often not necessary to perform the lookup for the information being sought.
Also, you can notice that the netstat command displays the current state of all of the connections on the device. Some of the states’ examples are:
- Listening: Connection is waiting for a reply from the foreign host.
- Established : Connection has been established already.
- Close_wait : Connection has been closed from the remote side and your computer might be waiting for leftover packets to arrive.
- Time_wait: Local endpoint has ended the connection. The connection is being kept around so that any delayed packets can be matched to the connection and handled appropriately.
Each entry under this command shows an IP address followed by a port number. You’ll see something like this —
Here, TCP is the protocol, 192.168.1.8 is the local IP address, 55544 is the local port number, 111.221.29.125 is the foreign IP address and 443 is the foreign port number while the connection is established already.
If you are aware of the port numbers then you can figure out from the above entry that it is a HTTPS connection to the IP address 111.221.29.125.
However, if you are also interested in knowing about the foreign address name instead of the IP address, just type netstat -a.
-
netstat -a
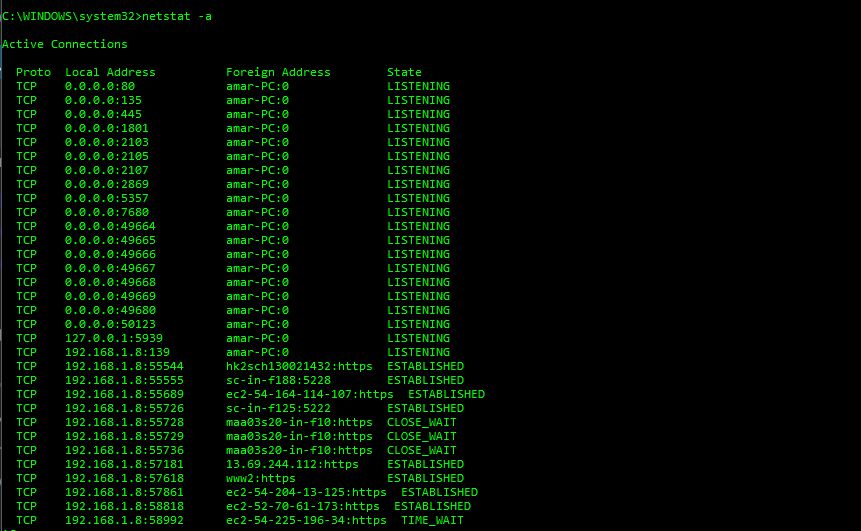
With this command, you can see all the active connections and instead of just showing the raw IP address of the foreign address, it does DNS lookup as well.
-
netstat -e
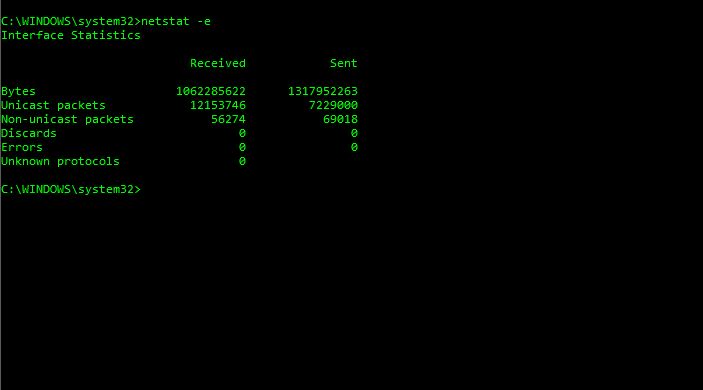
This command will show you statistics of the overall packets.
-
netstat -sp
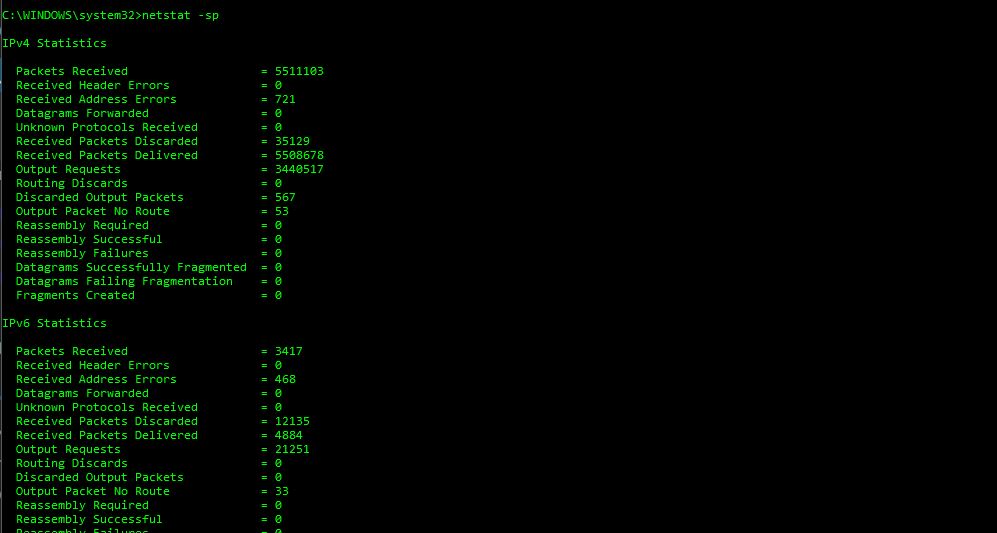
This netstat command shows you statistics per protocol. If you want to know the statistics for a particular protocol, you can follow the following variants of the netstat commands as shown below:
- netstat -sp ip for ipv4 statistics
- netstat -sp ipv6 for ipv6 statistics
- netstat -sp icmp for icmpv4 statistics
- netstat -sp tcp for tcp statistics of IPv4 etc.
www.extremehacking.org
Cyber Suraksha Abhiyan, CEHv9, CHFI, ECSAv9, CAST, ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v9 course in Pune-India, ceh certification in pune-India, ceh v9 training in Pune-India, Ethical Hacking Course in Pune-India
