Institute For Ethical Hacking Course and Ethical Hacking Training in Pune – India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan

Credits: ABC News
A malware similar in nature to Stuxnet but more aggressive and sophisticated allegedly hit the infrastructure and strategic networks in Iran.
Details about the supposed new attack are superficial at the moment, as there are no details about the supposed attack, the damage it caused or its targets.
Lightning striking twice in the same spot
A report on Wednesday from Israeli evening news bulletin Hadashot says that Iran “has admitted in the past few days that it is again facing a [Stuxnet-like] attack, from a more violent, more advanced and more sophisticated virus than before, that has hit infrastructure and strategic networks.”
The Iranian Supreme Leader Ayatollah Ali Khamenei in a televised speech on Sunday said that the country’s civil defenses should adapt to fight enemy infiltration via new threats.
On the same day, General Gholamreza Jalali, Iran’s head of the Passive Defense Organization that is charged with combating sabotage activity, was quoted by ISNA news agency saying that the agency discovered and neutralized “a new generation of Stuxnet which consisted of several parts” that was trying to breach Iranian systems.
Stuxnet is believed to be the creation of the intelligence agencies in the US and Israel. It is an advanced toolset specifically tailored to target Siemens industrial control system equipment. More specifically, it reprogrammed the PLCs (programmable logic controller) for centrifuges in nuclear enrichment at various facilities in Iran.
Built for sabotage purposes, the malware was stealthy in its actions and made it look like the damage it caused to the centrifuges was, in fact, the result of an accidental malfunction of the equipment.
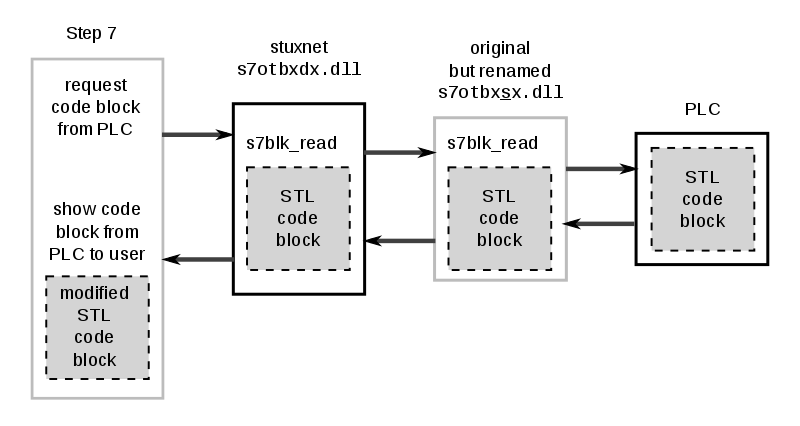
Considering the news coverage and attention received from several cybersecurity companies that analyzed its modules, Stuxnet is unlikely to emerge in a recognizable version. General Jalil could have referred to malware with destructive modules that attempted to infiltrate and attack Iranian infrastructure.
More Iranian context
The Hadashot report was preceded by a communication about Mossad intelligence agency stopping a murder plot targeting three Iranians in Denmark.
Before this, media outlets covered news about General Jalali saying that President Hassan Rouhani’s mobile phone had to be replaced recently with a more secure variant because it had been tapped.
The source of the information was the ISNA news agency quoting the Iranian official on Monday.
The Passive Defense Organization’s Public Relations Department dismissed the news as false, stating that the information was taken out of context.
The agency clarified that General Jalali’s remarks were a warning about the risk of interception in the case of unencrypted calls Iran’s officials make when abroad.
“Recently, some media outlets have published remarks by Brigadier General Gholamreza Jalali which were taken out of context with regard to the president’s mobile phone being tapped, which is strongly denied,” the statement read.
www.extremehacking.org
Sadik Shaikh | Cyber Suraksha Abhiyan, Ethical Hacking Training Institute, CEHv10,CHFI,ECSAv10,CAST,ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v10 course in Pune-India, ceh certification in pune-India, ceh v10 training in Pune-India, Ethical Hacking Course in Pune-India
