Institute For Ethical Hacking Course and Ethical Hacking Training in Pune – India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan

Credits: bleeping
The Internet Crime Complaint Center (IC3), in collaboration with the Department of Homeland Security and the FBI, have issued a security alert regarding attacks being conducted through the Windows Remote Desktop Protocol. While the most publicized attacks over RDP are related to ransomware, attackers also hack into exposed RDP services for corporate theft, installation of backdoors, or as a launching point for other attacks.
“Remote administration tools, such as Remote Desktop Protocol (RDP), as an attack vector has been on the rise since mid-late 2016 with the rise of dark markets selling RDP Access,” stated the alert from US-Cert. “Malicious cyber actors have developed methods of identifying and exploiting vulnerable RDP sessions over the Internet to compromise identities, steal login credentials, and ransom other sensitive information. The Federal Bureau of Investigation (FBI) and Department of Homeland Security (DHS) recommend businesses and private citizens review and understand what remote accesses their networks allow and take steps to reduce the likelihood of compromise, which may include disabling RDP if it is not needed.”
If you are a reader of BleepingComputer, then you already know that attackers are using remote desktop services to remotely gain access to networks and computers on them.
Last year, we covered how the xDedic criminal marketplace was selling hacked remote desktop services accounts for as little as $6 USD per server. The sale of RDP accounts on criminal markets continues to this day.
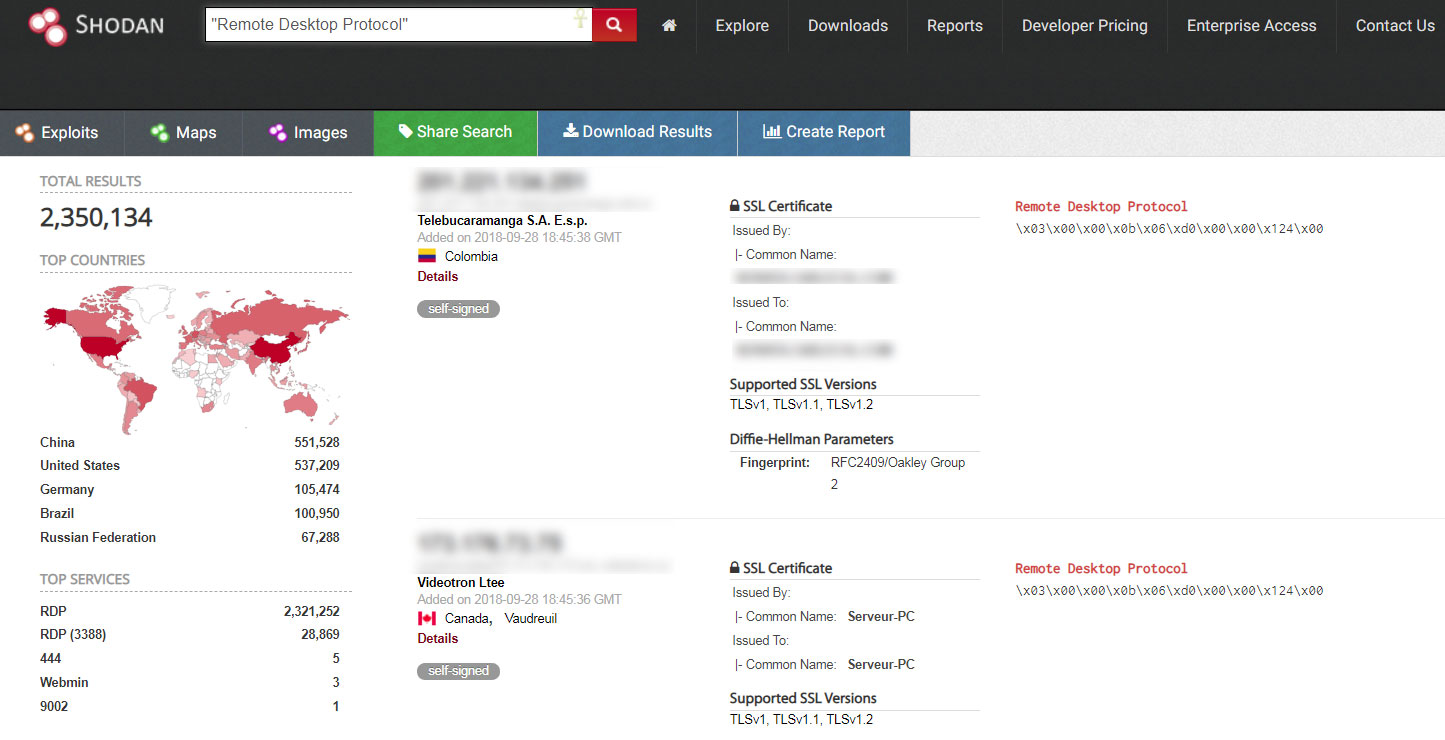
Shodan.io, a search engine for internet-connected devices, also shows that there are over 2 million computers running Remote Desktop and connected directly to the Internet. These servers are just waiting to be hacked.
We have also routinely covered how ransomware infections such as CrySiS/Dharma, SamSam, BitPaymer, and CryptON infect entire networks by hacking into public facing Remote Desktop servers over the Internet.
Because these attacks target entire networks, rather than an individual computer, and carry price tags of $3,000 – $5,000 USD to decrypt a single computer or upwards to $50,000 USD to decrypt an entire network, they tend to be highly publicized.
For example, the ransomware attacks at PGA of America, Port of San Diego, Atlanta, and numerous hospitals were all most likely executed through remote desktop servers being exposed on the Internet.
Therefore, it is very important that all organization that utilize RDP properly protect these services.
Protecting Remote Desktop Servers
Using Remote Desktop Services can be an integral resource for companies, so we are not saying that it should not be used. What we are saying is that if you use RDP, you need to protect it!
Below we have outlined various steps that should be performed to protect remote desktop servers from being attacked.
Never expose RDP servers directly to the Internet
RDP servers should never be connected directly to the Internet. Instead, organizations should place RDP servers behind a VPN, or firewall, so that only permitted users can access them.
Doing this also, makes it harder to find the servers and initiate brute force attacks, where attackers repeatedly login to a server while trying to guess the password.
If you can, you should also change the TCP port for RDP from the default port of 3389 to a non-standard one. This just adds a little security-by-obscurity flavor to the mix of protection methods.
Use strong passwords and multi-factor authentication
As Remote Desktop attacks are typically performed by attackers brute forcing passwords until they guess the right one, it is important that all users have strong and complex passwords. This can be enforced using strong password policies in Windows.
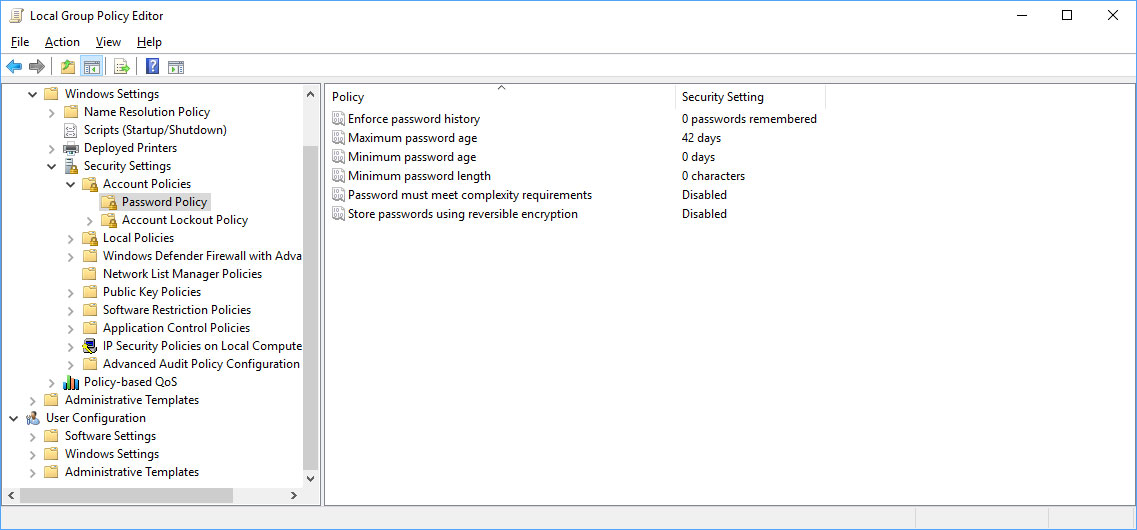
To further increase protection, organizations should also look into adding multi-factor authentication to domain logins.
Enable account lockout policies
Brute force attacks can generally be prevented by using account lockout policies. These policies temporarily make it so an account cannot logged into after having a certain amount of failed login attempts.
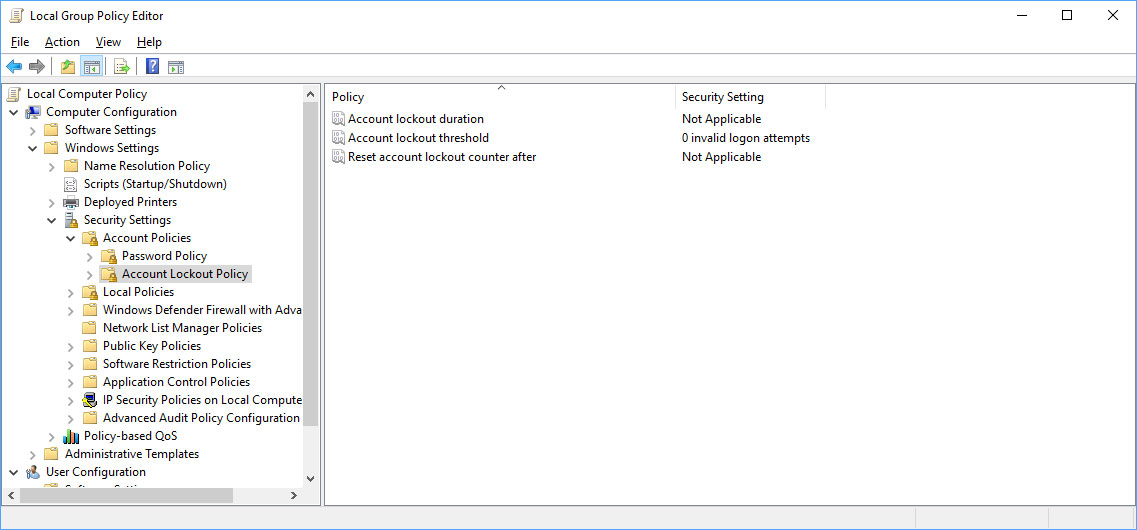
As brute force attacks rely on repeatedly attempting to login to an account with different passwords, using lock out policies prevents this.
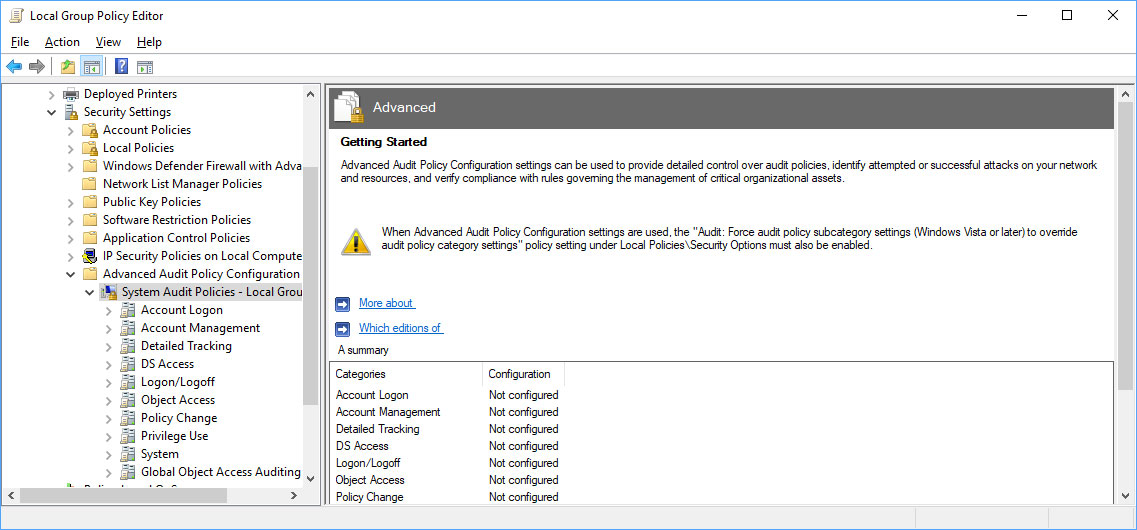
Enable the auditing of account logins
By enabling account audit policies, administrators can get insight into what accounts are having repeated failed login attempts. This allows admins to pinpoint accounts that may be targeted for attacks.
Install security updates
Finally, and not least in importance, update, update, update. I know it is hard for some companies to install security updates as soon as they come out, but they should be installed as soon as possible.
www.extremehacking.org
Sadik Shaikh | Cyber Suraksha Abhiyan, Ethical Hacking Training Institute, CEHv10,CHFI,ECSAv10,CAST,ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v10 course in Pune-India, ceh certification in pune-India, ceh v10 training in Pune-India, Ethical Hacking Course in Pune-India
