Ethical Hacking Institute Course in Pune-India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan
TOR browser is used by hundreds of thousands of users — activists, journalists, hackers, and more — all around the world. This anonymity software suite ensures that people are able to save themselves from the prying eyes of governments and hackers. It ensures a good level of privacy, making it difficult to reveal the real I.P. address of the users.
Honeypot and fingerprinting techniques have made TOR vulnerable
TOR browser is a preconfigured Firefox browser modified to protect the users’ privacy and identity while browsing the web. In the browser, plugins are disabled, history and cache aren’t recorded, and everything is erased as you close the browser. However, with time, multiple techniques like TOR Honeypot and Traffic Fingerprinting have emerged that make TOR by no means enough to protect users privacy on the web.
Along the similar lines, an independent security researcher Jose Carlos Norte has found a set of new fingerprinting ways to uncover the identity of TOR users. The TOR user fingerprinting methods refer to the ways of tracking some non-standard details about user behaviour. Using fingerprinting, the browsing behaviour of a TOR user can be compared to his/her browsing patterns while the user is surfing the same website on a regular browser.
JavaScript can give a TOR user’s identity away
On his blog, Mr. Norte has published different TOR user fingerprinting techniques. One such technique deals with running a CPU-intensive JavaScript operation in the web browser and recording the time needed to execute the task. This information could be later used to identify the suspects who are using TOR browser.
Another technique uses getClientRects JavaScript function. Norte calls it the most interesting TOR user fingerprinting vector found on TOR Browser as it returns the exact pixel position and size of a DOM element’s rectangular box. This detail is important because this function returns different value and accuracy that’s dependent on the user’s fonts, screen resolution, and other hardware and software settings.
Your mouse movements can reveal your true identity
You’ll be surprised to know that your mouse movements can give your identity away. The first technique deals with identifying the mouse scrolling speed. Based on the scrolling speed and user behaviour patterns, an attacker can record user data and use it to pinpoint a TOR user.
Norte has even created a page where he demonstrates his research.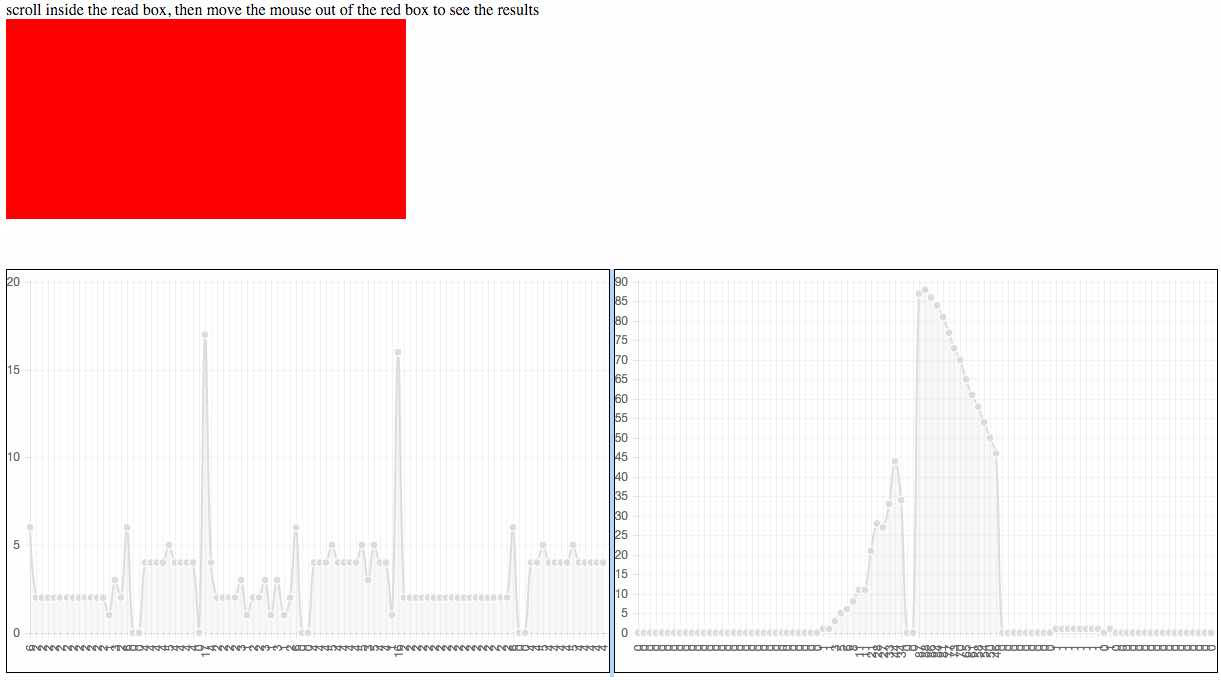
An attacker can also log the speed at which you move your mouse cursor across the page. This technique gathers more data from your mouse sensitivity preferences and gestures, this technique is more accurate that the previous one. Just in case you are using a trackpad, this technique is even more lethal.
“It is easy to fingerprint users using tor browser to track their activity online and correlate their visits to different pages. getClientrects provides a very interesting vector for TOR user fingerprinting. The CPU benchmark and the Mouse wheel and mouse speed methods provide even more information to distinguish between similar users,” he concludes.
You can read more about these TOR user fingerprinting techniques at his blog.
www.extremehacking.org
Cyber Suraksha Abhiyan, CEHv9, CHFI, ECSAv9, CAST, ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v9 course in Pune-India, ceh certification in pune-India, ceh v9 training in Pune-India, Ethical Hacking Course in Pune-India
