Ethical Hacking Institute Course in Pune-India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan
In the world of mobile apps, if you are looking for malware, there are apps (yes, plural) for that. How about one that leaks sensitive content? There are apps for that, too. Pick any other mobile attack vector; chances are there is an app for that as well. Regardless of how well your Mobile Device Management (MDM) policies are set up, if mobile apps are not part of your equation, then you are missing a big piece of the problem. After all, a smartphone is only as secure as the most insecure app on it.
A smartphone is only as secure as the most insecure app on it
And with millions of mobile apps to choose from, it seems that the next big opening into your network might just be an app away. To get a sense of how bad this problem is, all you have to do is look around for mobile app reputation services. There is literally a cottage industry built around recommending whether a mobile app is good, bad or ugly.
When we set out to tackle this problem, we identified four areas where Nessus could add value. First, provide a way to review which mobile apps were installed on which mobile devices. Second, provide a way to determine whether all required apps are installed. Third, provide a way to verify that only whitelisted apps are installed. And finally flag any non-approved or blacklisted apps. Nessus meets all these requirements.
Setup
To use this feature, simply upgrade to Nessus, use the MDM Configtemplate, and follow the wizard to set up the scan. The existing MDM .audit policies were updated to audit mobile apps to do the job for you.
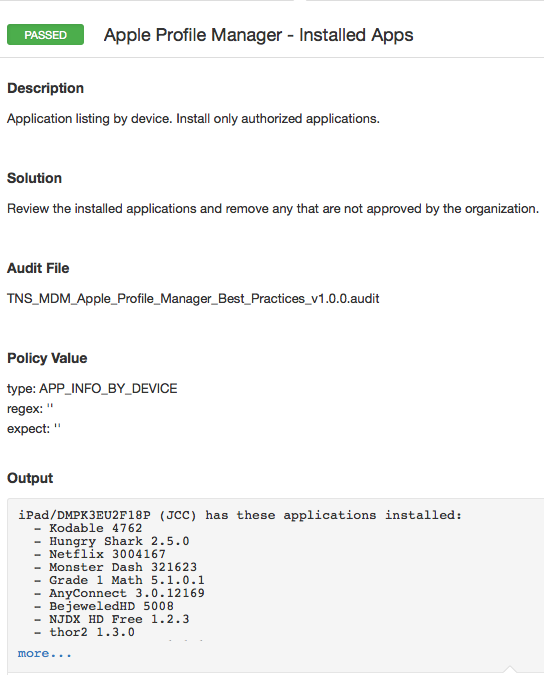
Installed apps
The Nessus MDM audit policies are updated in version to report on all installed apps.
Before you can start creating a policy around mobile apps, you first need to know what kinds of apps are installed on the mobile devices. The Nessus MDM audit policies are updated in version 6.5 to report on all installed apps.
Required apps
As you start tightening your mobile app policy, you may want to make sure that certain apps are installed on all mobile devices managed by your organization. For example, you may have a requirement to have an anti-virus app or a VPN app installed on all devices. The updated audit policies will help you do that.
Whitelisted apps
Another variant of the required apps feature is the whitelisted apps feature. For example, your organization might decide to approve any app from Google. Therefore instead of approving each individual app, you could have a blanket approval for all apps from Google with a filter such as Google .+. Any app that is not part of the whitelisted pool of apps will be flagged.
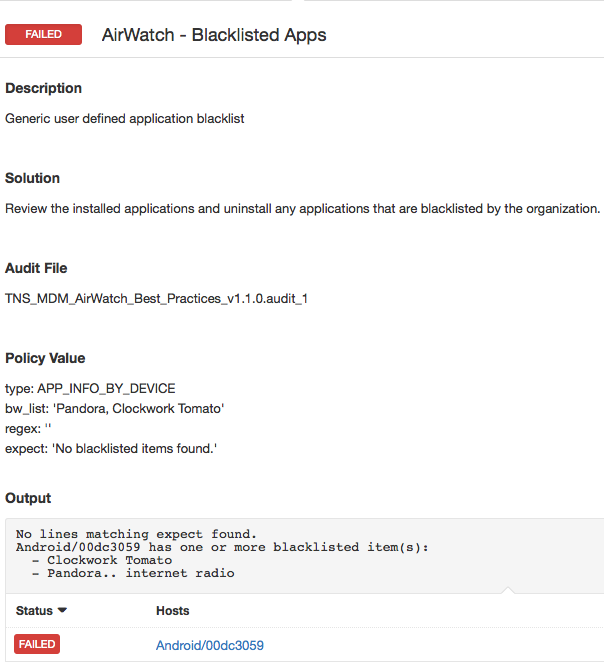
Blacklisted apps
And finally, there are certain apps which shouldn’t be installed on mobile devices under any circumstance. This could be due to concerns around malware, privacy or even network bandwidth consumption. Any app that is part of a blacklisted pool of apps will be flagged.
XcodeGhost affected apps
The updated audit policies will also help you look for XcodeGhost affected apps.
Sometimes the best features write themselves and the use cases for them just drop out of the sky. When we set out to implement the blacklisted apps feature in 6.5, XcodeGhost was not even on our minds, and yet when Nessus 6.5 ships, this might be the most important use case for this new feature. The updated audit policies will also help you look for XcodeGhost affected apps.
How are whitelist/blacklisted apps defined?
Now that you know it’s possible to create a blacklisted/whitelisted pool of apps in Nesssus 6.5, the next question you may have is how does one go about configuring these apps? The answer is pretty straightforward. The list is essentially a comma-separated list of apps configurable through the Nessus UI for that specific .audit.
Here’s an example:
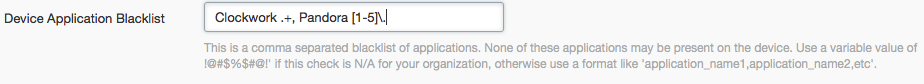
Note that it also accepts and regexes version numbers, which is a very powerful way to blanket approve/disapprove apps either by app name or version number. By default, the lists are not defined (.*) and will report a PASS result.
Which MDMs are supported?
Nessus 6.4 includes MDM auditing capabilities for MobileIron and AirWatch, and Nessus 6.5 extends those capabilities to audit Mobile Apps. Nessus 6.5 also includes the ability to audit mobile apps with Apple Profile Manager.
Sample

www.extremehacking.org
Cyber Suraksha Abhiyan, CEHv9, CHFI, ECSAv9, CAST, ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v9 course in Pune-India, ceh certification in pune-India, ceh v9 training in Pune-India, Ethical Hacking Course in Pune-India
