Ethical Hacking Institute Course in Pune-India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan
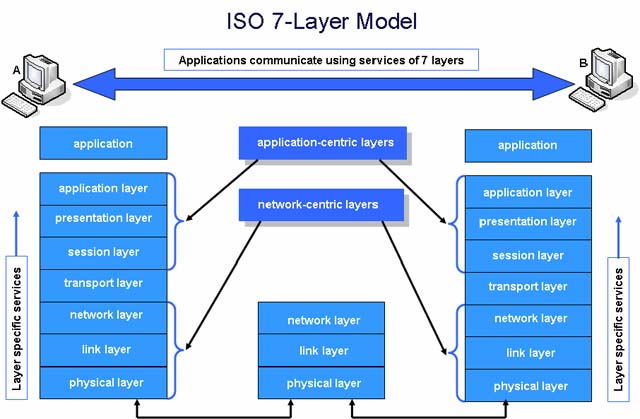
As we talked earlier in the article OSI Model and its 7 layers, the application layer becomes one of the most important layers of the OSI model because it is fundamentally responsible for the communication of the applications running at the applicaiton layer.
Application Layer:
Application is the last layer in the OSI model and here are some of the protocol functionalities of the application layer:
-
Domain name service Protocol
We always remember the name of a website, not their IP address because IP addresses are very hard to remember. It’s more or less like not remembering the mobile number of a person instead saving that number by a name.
The domain name service protocol working at the application layer translates the domain names IP addresses for us.
-
Hypertext Transfer Protocol (HTTP)
HTTP protocol defines how messages are formatted and transmitted over the internet. HTTP has different status codes that tell what actions needs to be taken by the web servers and browsers in response to various commands.
For example, HTTP 404 is used when the resource in not found.
-
Simple Mail Transfer Protocol (SMTP)
SMTP stands for Simple Mail Transfer Protocol. This protocol is used in delivering an email from an email client, such as Outlook Express, to an email server or when email is delivered from one email server to another. SMTP uses port 25.
-
Telnet
Telnet protocol is used to login to a remote server and it provides a bidirectional interactive text-oriented communication facility using a virtual terminal connection.
Telnet is one of the best examples of the client-server protocol. This protocol is based on a reliable connection-oriented transport. Typically, this protocol is used to establish a connection to Transmission Control Protocol (TCP) port number 23, where a Telnet server application (telnetd) is listening. Telnet, however, predates TCP/IP and was originally run over Network Control Program (NCP) protocols.
-
Simple Network Management Protocol (SNMP)
A network admin uses many devices to run a network. Simple Network Management Protocol (SNMP) is an Internet-standard protocol for network management. SNMP is used by network admins mostly for collecting and organizing information about managed devices on IP networks and for modifying that information to change device behavior. Devices that typically support SNMP include most of the networking devices such as routers, switches, servers, workstations, printers, modem racks and more.
-
BOOTP
When a network device or a computer is powered up the first thing it does is the booting up its operating system. BOOTP protocol is used for the same for the devices connected over to a network. When a computer that is connected to a network is powered up, the system software broadcasts BOOTP messages onto the network to request an IP address assignment and it also notifies other devices that a particular device has woken up. A BOOTP configuration server assigns an IP address based on the request from a pool of addresses configured by an administrator.
Some of the famous protocols which run on the Application layer are:
- BitCoin
- BitTorrent
- Finger
- FreeNet
- Gopher
- HTTP
- Telnet
- SNMP
- SMTP
- MIME
- NFS
- SIP
- SDP
- XMPP etc.
Enjoy!!!!
www.extremehacking.org
Cyber Suraksha Abhiyan, CEHv9, CHFI, ECSAv9, CAST, ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v9 course in Pune-India, ceh certification in pune-India, ceh v9 training in Pune-India, Ethical Hacking Course in Pune-India
