Extreme Hacking | Sadik Shaikh
Advanced Ethical Hacking Institute Course in Pune
Credits: OTW
Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.
For those of you who are new here, a denial of service is basically a simple attack that keeps the target system from operating as it should. In its simplest form, it uses up all of the system resources so that others can’t connect. More sophisticated attacks will cause the system to crash or create a infinite loop that uses all of the system’s CPU cycles.
In general, a DoS attack is the easiest and least sophisticated type of attack. Some have gone so far as to say that an eight-year-old could participate in a DoS attack, and there is some truth to that statement since some tools make it as easy as putting in an IP address and hitting “Start.”
In recent years, DoS and DDoS attacks (the latter of which involves more than one attack source) have been growing rapidly and more and more companies/websites are employing specialized anti-DoS tools and techniques (among the most popular and most expensive is Incapsula).
In this article, I want to lay some groundwork on the techniques for DoSing and provide you with some of the tools to do so. Before we do that, though, I want to point out that some of the tools we have already explored here on Null Byte are useful for DoS attacks, including Hping, Nmap, Metasploit, and even Aircrack-ng (for DoSing wireless access points).
Methods
You can categorize denial-of-service attacks into at least three different types, which include:
- Volume-Based
These are the simplest attacks. The attacker simply sends a large volume of packets to the target thereby using up all the resources. The resources used might simply be bandwidth. These attacks include ICMP and UDP floods.
- Protocol-Based
These attacks often use the server’s resources rather than bandwidth going to and from of the server. They can also use the resources of the network equipment on the periphery of the server (such a firewalls, intrusion detection systems, and switches). Examples include Smurf attacks (ICMP to a broadcast IP with a spoofed IP), Fraggle attacks (same as the Smurf, only using UDP), SYN floods, ping of deaths (oversized ICMP with the same destination and source IP and port), and many others.
- Application Layer Attacks
These attacks are compromised of what appear to be legitimate application layer (layer 7) requests to the server that are intended to crash it. These include attacks on Apache HTTP Server and Microsoft IIS, and includes tools such as Slowloris.
DoS & DDoS Tools
There are literally hundreds of DoS and DDoS tools available. Within Kali, we can find auxiliary modules within Metasploit specifically for DoSing. If we navigate to:
kali > cd /usr/share/metasplot-framework/auxiliary/dos
And list the contents of that directory, we can see that Metasploit has organized its DoS tools by the type of target. There are hundreds of denial-of-service tools in Metasploit.
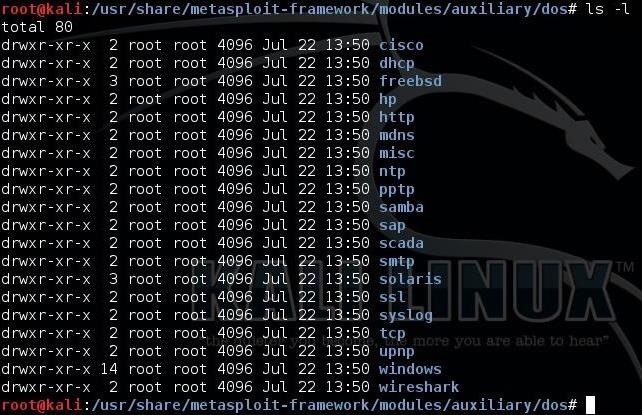
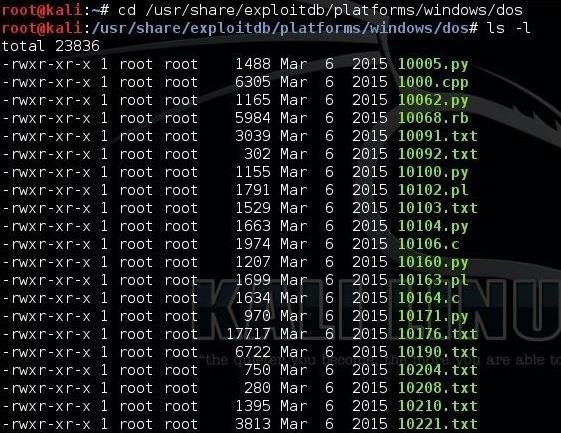
We can also find hundreds of DoS tools in the Exploit Database built into Kali, and still more at Exploit-DB.com. We can find a listing of the Exploit-DB DoS tools by navigating to:
kali > /usr/share/exploitdb/platforms/windows/dos
A long listing (ls -l) of this directory lists all of the Windows DoS tools. A similar, shorter list is at /usr/share/exploitdb/platforms/Linux/dos.
Some of the Most Popular DoS Tools
There is no way I can list and evaluate every DoS tool, but here is a limited list of some of the most popular and effective. This is far from an exhaustive list, but I hope to give you the basics on some of the most popular DoS and DDoS tools. If you have a favorite, by all means, please put it in the comments with a link to the download.
One quick note of warning: Be very careful when looking online for DoS or DDoS tools. Many of them simply take you to a malicious link and will install a trojan on your system. I don’t know anyone who would do that. 😉
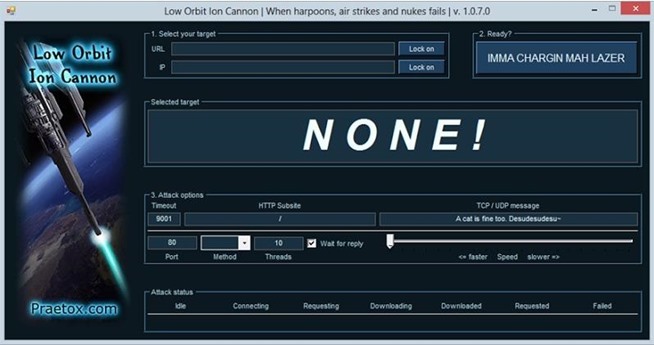
1. LOIC
The Low Orbit Ion Cannon (LOIC) may be the most popular DoS tool and has made its way into hacker lore. It is capable of sending mass amounts of ICMP or UDP packets to the target, thereby saturating the bandwidth, and has been used in some of the most effective and notorious DoS attacks.
LOIC was effectively used by 4chan in the Project Chanology attack on the Church of Scientology website in 2009, and by Anonymous in the Operation Payback attack against PayPal, Visa, and MasterCard in retaliation for cutting off WikiLeaks donations.
LOIC attacks can be largely mitigated by limiting UDP and ICMP packets and limiting how many packets can be sent and delivered to any one client. You can download LOIC on SourceForge. This tool is Windows-based and almost as easy as pointing and clicking.
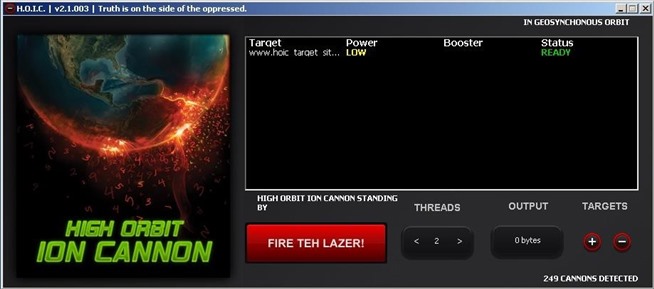
2. HOIC
The HOIC was developed during Operation Payback by Praetox—the same folks who developed LOIC. The key difference is that HOIC uses a HTTP flood using booster files that enable a small number of users to effectively DoS a website by sending a flood of randomized HTTP GET and POST requests. It is capable of simultaneously DoSing up to 256 domains. You can download it from SourceForge.
3. XOIC
XOIC is another easy-to-use DoS tool. The user simply needs to set the IP address and port of the target, select a protocol (HTTP, UDP, ICMP, or TCP), then begin to fire away! You can download it on SourceForge
5. HULK
HTTP Unbearable Load King, or HULK, is another tool capable of bringing down web servers. This tool uses various obfuscation techniques to limit the ability of the target to mitigate the attack. You can download it onPacket Storm.
6. UDP Flooder
UDP Flooder does just as you would expect—it sends a flood of UDP packets to the target. It has been effectively used to knock gamers off their networks (online games primarily use UDP). You can download it atSourceForge.
7. RUDY
R-U-Dead-Yet, or RUDY, takes a different approach to DoSing websites. It enables the user to select a form from the web app and then use that form to send a flood of POST requests. You can download it from Hybrid Security.
8. ToR’s Hammer
ToR’s Hammer was designed to be run through the ToR network to anonymize the attack and limit mitigation. The problem with this strategy is that the ToR network tends to be very slow, thereby limiting the rate at which the packets can be sent and thereby limiting the effectiveness of this tool. You can download it from Packet Storm or SourceForge.
9. Pyloris
Pyloris is another DoS tool, but with still a different strategy. It allows the user to construct their own, unique HTTP request headers. It then attempts to keep open these TCP connections as long as possible in order to exhaust the connection queue. When it does this, no legitimate connections can be made and new attempts to connect by other users will be dropped. You can download it on SourceForge.
10. OWASP Switchblade
The Open Web Application Security Project (OWASP) and ProactiveRISK developed the Switchblade DoS tool to be used to test the resiliency of a web app to DoS attempts. It has three modes, 1. SSL Half-Open, 2. HTTP Post, and 3. Slowloris. You can download it from OWASP.
11. DAVOSET
DAVOSET (DDoS attacks via other sites execution tool) is a DDoS tool, written in Perl, that uses zombie systems to distribute the attack across multiple systems. This tool uses Abuse of Functionality and XML External Entities vulnerabilities on other sites to “zombie” them and attack the target site. It includes over 160 zombie services. You can download it from Packet Storm or GitHub.
12. GoldenEye HTTP DoS Tool
GoldenEye is simple DoS tool that loads an HTTP server attempting to exhaust its resource pool. It’s great for testing your website, but not really effective in the real world as most perimeter defenses will detect it. You can download it from GitHub.
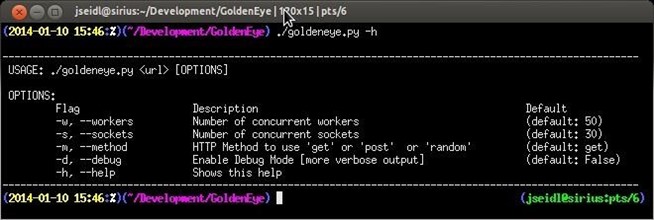
13. THC-SSL-DOS
This DDoS tool (built right into Kali) is different from most DoS tools in that it doesn’t require huge amounts of bandwidth and can be conducted with a single system. It attacks vulnerabilities in SSL to bring down the server. You can download it from THC, but if you are using Kali, you already have it.
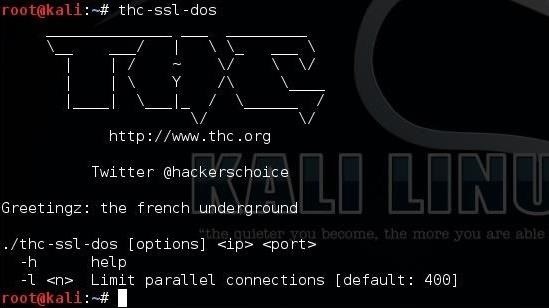
14. DDOSIM – Layer 7 DDoS Simulator
This tool from Storm Security simulates a DDoS attack from various zombies with random IP addresses. It attempts to create a full TCP connection (SYN-SYN/ACK-ACK). As the name implies, it operates at the application layer (layer 7). It is also capable of simulating a DDoS attack upon the SMTP server and a TCP flood at random ports. You can download it from SourceForge.
www.extremehacking.org
CEHv9 CHFI ECSAv9 CAST ENSA CCNA CCNA SECURITY MCITP RHCE CHECKPOINT ASA FIREWALL VMWARE CLOUD ANDROID IPHONE NETWORKING HARDWARE TRAINING INSTITUTE IN PUNE,Certified Ethical Hacking, Center For Advanced Security Training in India,IT Security Training Information Security Traning Courses in Pune, ceh certification in pune, Ethical Hacking Course in Pune
