Institute For Ethical Hacking Course and Ethical Hacking Training in Pune – India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan
Credits: securityaffairs
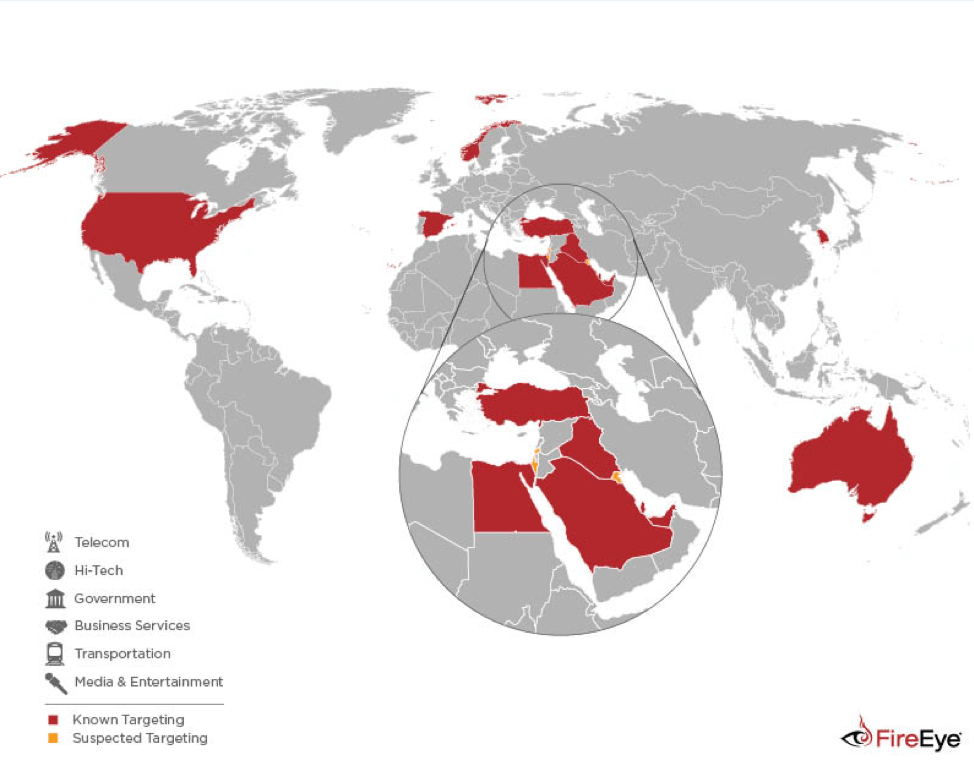
The APT39 cyberespionage group is carrying out a widespread campaign using a broad range of custom and off-the-shelf tools. The group has been active at least since November 2014, its operations are aligned with the ones attributed to the Chafer group and OilRig groups, it brings together TTPs used by both actors.
APT39 cyber spies focused their operations in the Middle East, other entities targeted by the group are the U.S. and South Korea. Most of the victims belong to the telecommunications and travel industries, cyber spies also targeted high-tech industry and government.
“APT39 primarily leverages the SEAWEED and CACHEMONEY backdoors along with a specific variant of the POWBAT backdoor. While APT39’s targeting scope is global, its activities are concentrated in the Middle East.” reads the report published by FireEye.
“APT39 has prioritized the telecommunications sector, with additional targeting of the travel industry and IT firms that support it and the high-tech industry.”
The operations collected by the APT39 group aims to collect geopolitical data along with monitoring targets of interest.
Experts observed an overlap between malware distribution techniques and command and control infrastructures used by APT39 and the ones observed in campaign associated with other Iran-linked APT groups.
Researchers at FireEye pointed out that the POWBAT backdoor used by the APT39 group is different from the one used by the APT34, but they don’t exclude a close collaboration between the two crews collaborate.
“While APT39 and APT34 share some similarities, including malware distribution methods, POWBAT backdoor use, infrastructure nomenclature, and targeting overlaps, we consider APT39 to be distinct from APT34 given its use of a different POWBAT variant. It is possible that these groups work together or share resources at some level.” continues the report.
Initial compromise leverages spear-phishing messages using malicious attachments or including URLs that point to a POWBAT infection. Furthermore, cyberspies also target vulnerable web servers of organizations to install web shells such as ANTAK and ASPXSPY, attackers used stolen legitimate credentials to compromise externally facing Outlook Web Access (OWA) resources.
In the post-infection phase, the threat actors leverage custom backdoors such as SEAWEED, CACHEMONEY, and a unique variant of POWBAT that is used by attackers to gain a foothold in a target environment.
Attackers use tools like Mimikatz and Ncrack, along with legitimate tools such as Windows Credential Editor and ProcDump and the port scanner BLUETORCH.
Once inside the target environment, for lateral movement that attackers use tools such as Remote Desktop Protocol (RDP), Secure Shell (SSH), PsExec, RemCom, and xCmdSvc. Other custom tools used by the threat actors are as REDTRIP, PINKTRIP, and BLUETRIP that allow them to create SOCKS5 proxies between infected hosts.
APT39 use to compress data using WinRAR or 7-Zip before exfiltrating it.
“APT39’s targeting not only represents a threat to known targeted industries, but it extends to these organizations’ clientele, which includes a wide variety of sectors and individuals on a global scale.” FireEye concludes.
“APT39’s activity showcases Iran’s potential global operational reach and how it uses cyber operations as a low-cost and effective tool to facilitate the collection of key data on perceived national security threats and gain advantages against regional and global rivals,”
www.extremehacking.org
Sadik Shaikh | Cyber Suraksha Abhiyan, Ethical Hacking Training Institute, CEHv10,CHFI,ECSAv10,CAST,ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v10 course in Pune-India, ceh certification in pune-India, ceh v10 training in Pune-India, Ethical Hacking Course in Pune-India
