Institute For Ethical Hacking Course and Ethical Hacking Training in Pune – India
Extreme Hacking | Sadik Shaikh | Cyber Suraksha Abhiyan
Credits: theregister
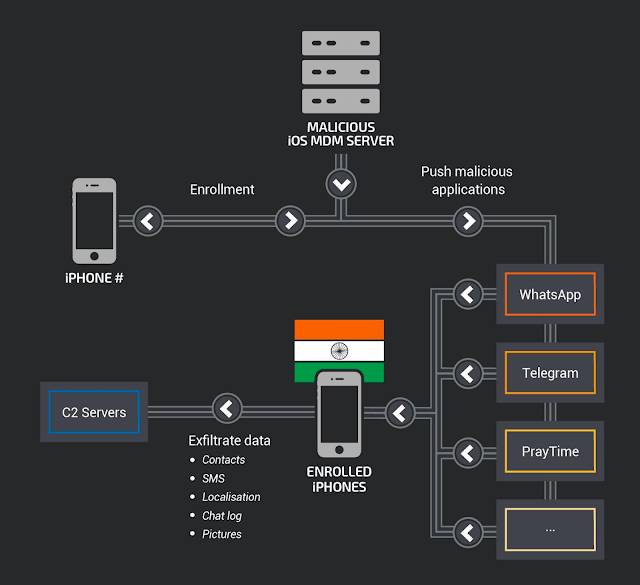
Business iPhone users in India have been targeted in a sophisticated and attack run through bogus Mobile Device Management (MDM) servers.
Using either physical access or – more likely – social engineering trickery, certificates from a selection of two sketchy MDM servers were installed on targeted iPhones. This gave the hacker-controlled MDMs admin rights that were abused to load bogus versions of WhatsApp, Telegram and other apps, security researchers said.
Data including emails, SMSes and other messages sent through enrolled smartphones was subsequently uploaded to systems under the control of hackers.
Attackers set up an open-source MDM and used this to deploy malicious code into secure chat applications such as Telegram and WhatsApps in order to surreptitiously retrieve messages/chats and photos.
The counterfeit apps also allowed the hackers to track the location of compromised smartphones, as a blog post by Cisco Talos explains.
The attacker used the BOptions sideloading technique to add features to legitimate apps, including the messaging apps WhatsApp and Telegram, that were then deployed by the MDM onto the 13 targeted devices in India. The purpose of the BOptions sideloading technique is to inject a dynamic library in the application.
The malicious code inserted into these apps is capable of collecting and exfiltrating information from the device, such as the phone number, serial number, location, contacts, user photos, SMS and Telegram and WhatsApp chat messages. Such information can be used to manipulate a victim or even use it for blackmail or bribery.
HackingTeam, a Milan-based law enforcement snoopware supplier, has previously used the same technique but there is no evidence to implicate it, and the use of an Indian-registered mobile phone and other factors point to a local attacker, according to Cisco Talos.
The attacker tried to mimic Russian hackers by using mail.ru email but Cisco Talos found testing devices enrolled on the MDM with an Indian phone number and registered on an Indian provider.
The threat intel crew has worked closely with Apple to counter the threat. Apple had already pulled three digital certificates associated with the hacking group before Cisco Talos got involved. Two other digital certificates were revoked shortly afterwards.
Log analysis of files left on the MDM servers and the malware’s command-and-control (C2) server revealed that the malicious code had run since August 2015.
MDM is an enterprise-focused technology designed to allow sysadmins to control the setup and apps that run on corporate smartphones or to lock up a device in the event of either theft or loss.
Cisco Talos warned: “Users must be aware that accepting an MDM certificate is equivalent to allowing someone administrator access to their device, passwords, etc. This must be done with great care in order to avoid security issues and should not be something the average home user does.
“The likely use of social engineering to recruit devices serves as a reminder that users need to be wary of clicking on unsolicited links and verify identities and legitimacy of requests to access devices,” it added.
Over a three-year period, the attackers remained under the radar — likely due to the low number of compromised devices. For now it’s unclear who the targets of the campaign were – much less the perpetrator of the attack or its purpose
www.extremehacking.org
Sadik Shaikh | Cyber Suraksha Abhiyan, Ethical Hacking Training Institute, CEHv10,CHFI,ECSAv10,CAST,ENSA, CCNA, CCNA SECURITY,MCITP,RHCE,CHECKPOINT, ASA FIREWALL,VMWARE,CLOUD,ANDROID,IPHONE,NETWORKING HARDWARE,TRAINING INSTITUTE IN PUNE, Certified Ethical Hacking,Center For Advanced Security Training in India, ceh v10 course in Pune-India, ceh certification in pune-India, ceh v10 training in Pune-India, Ethical Hacking Course in Pune-India
